Introduction To Authorization
Introduction to Authorization
- Authentication: Who You Are ?
- Authorization: What You Are Allow To Do
Owasp API TOP 10 - 2019
| OWASP CATEGORY | Name |
|---|---|
| API1 | Broken Object Level Authorization |
| API2 | Broken User Authentication |
| API3 | Excessive Data Exposure |
| API4 | Lack of Resources and Rate Limiting |
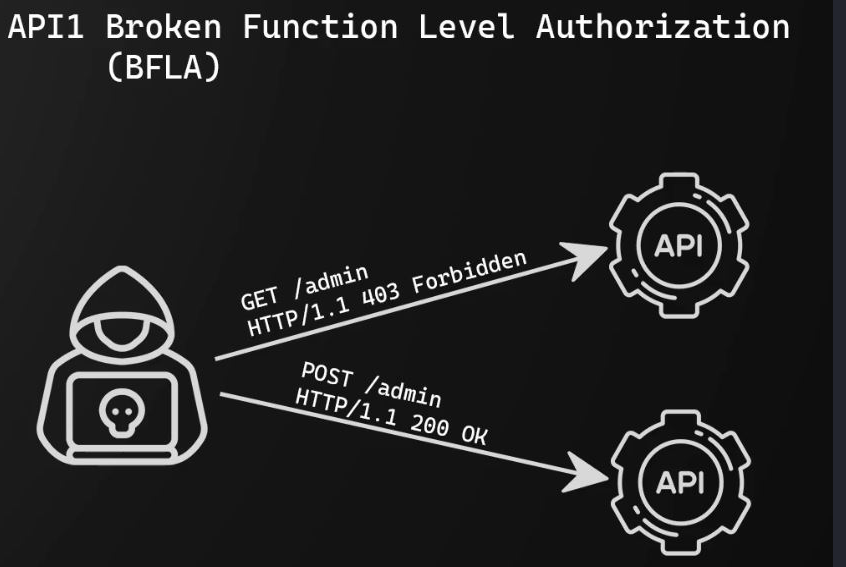
| API5 | Broken Function Level Authorization |
| API6 | Mass Assignment |
| API7 | Security Misconfiguration |
| API8 | Injection |
| API9 | Improper Assets Management |
| API10 | Insufficient Logging and Monitoring |